A comprehensive defense-in-depth strategy requires security mechanisms to be applied through the implementation of hardware, software and security policies. Hardware protection includes, but is not limited to, the implementation of next generation firewalls (NGFW), intrusion prevention systems/intrusion detection systems (IPS/IDS) and secure Web gateways (SWG). Software-based protection is done through anti-virus software deployments, automated patch management or tools for Internet monitoring. Finally, no defense-in-depth strategy would be complete without the implementation of strong security policies that prescribe processes for incident reporting, service and system audits, and security awareness training.
Take a Look at the DNS Layer
An often overlooked component of a defense-in-depth strategy is addressing security at the Domain Name System (DNS) layer. DNS is involved in nearly every transaction conducted on the Internet. It translates online queries into a set of navigation instructions to get you to the location requested. Recently, more and more organizations have begun to implement mechanisms to protect the DNS layer as it can be considered the “first line of defense” when preventing access to unwanted systems online.
Since nearly all communications on the Internet are initiated through a DNS lookup, implementing a security mechanism at this layer ensures that access to unwanted content can be controlled at the first point of engagement regardless of the port that the resulting communication is intended to traverse. For example, if a malicious bot is attempting to connect to its command-and-control point via an Internet Control Message Protocol (ICMP) request before executing its intended set of instructions, a DNS lookup is made first to determine the appropriate routing. If that lookup is blocked, the ICMP request will not be processed and the bot is stopped in its tracks.
Verisign DNS Firewall
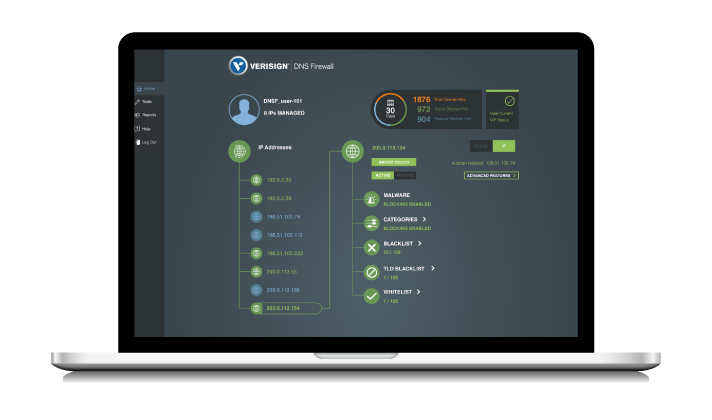
When expanding your defense-in-depth strategy to address the DNS layer, consider Verisign DNS Firewall. Verisign DNS Firewall is a cloud-based network security and threat intelligence service built upon Verisign’s global recursive DNS platform that offers robust protection from unwanted content and malware, as well as customizable filtering down to the individual DNS level.
A strong defense-in-depth strategy is one that is implemented in layers. Make sure you don’t ignore the DNS layer. To learn more about Verisign DNS Firewall, read Ovum Consulting’s recent report, “On the Radar – Verisign DNS Firewall.”




